
Trojan-toting trickbot comes out swinging after lying low for two years: Check Point Software


Cybersecurity solutions provider Check Point Software Technologies Ltd’s research has said that April saw the return of banking trojan trickbot on the global list of top 10 most wanted malware after almost two years. Trickbot was the month’s eighth most prevalent malware variant, returning with new capabilities, features and distribution vectors, the company said in a statement, adding that trickbot offers a high level of flexibility and customisation, which enables it to be distributed as part of multi-purpose campaigns.
The company also said that trickbots were used in several campaigns in April timed to coincide with Tax Day in the US, which is the day on which individual income tax returns are due to be submitted. In some of these campaigns, attackers had sent emails with Excel files attached, which downloaded trickbot to victims’ computers.

Once downloaded, trickbots could spread inside the network and steal banking details and confidential tax documents for fraudulent use.
Although cryptominers still occupied the top three positions on the global index, the remaining seven malware types among April’s top 10 were multi-purpose trojans, which is especially bothersome given the fact that they may be used not only to steal private data and credentials, but also for other nefarious purposes. In the past, Emotet and Trickbot were also used to populate the Ryuk ransomware, for example. As these malware constantly morph, enterprises must have a robust line of defence against them, equipped with advanced threat prevention.
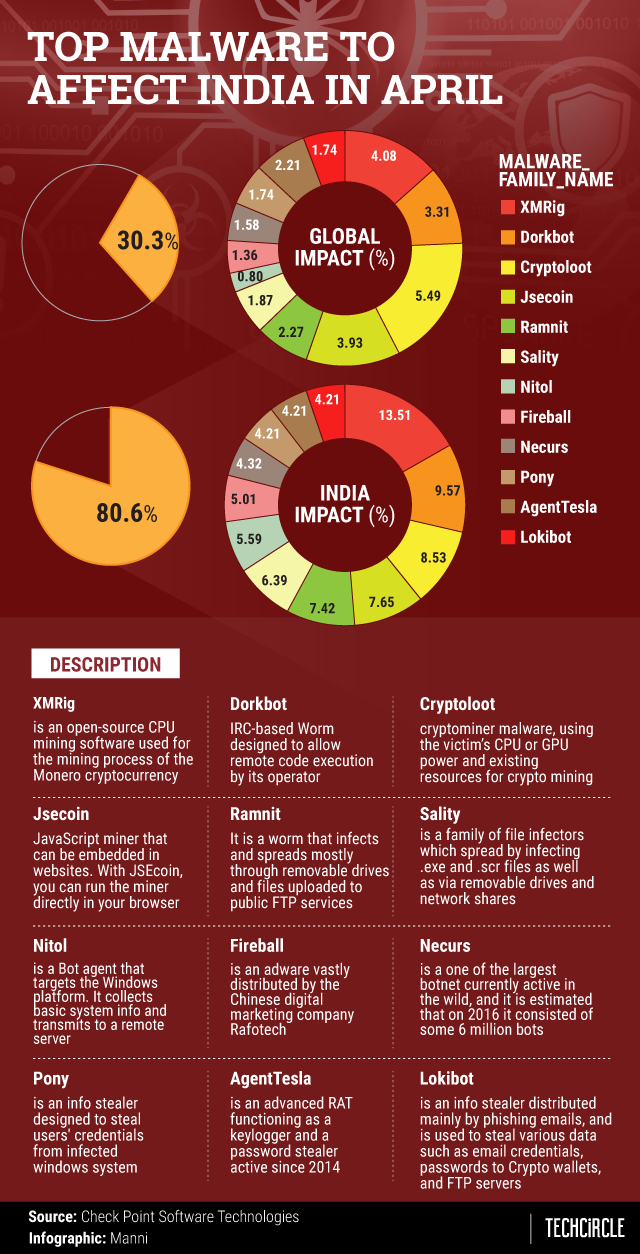
For India, XMRig, an open-source CPU mining software used for the mining process of the Monero cryptocurrency, took the first spot. Dorkbot and Cryptoloot followed.

Dorkbot, which spreads through instant messaging, USB drives, websites and social media channels like Facebook, is designed to allow remote code execution by its operator with the primary motivation being to steal sensitive information and launch denial-of-service attacks. Cryptoloot is a cryptominer malware that uses the victim’s CPU or GPU power and existing resources for cryptomining, adding transactions to the blockchain and releasing new currency.
The research also said that Triada was the most prevalent mobile malware in April followed by Hiddad and Lootor. While Triada is a modular backdoor for Android that grants super-user privileges to downloaded malware, Lotoor is a hack tool that exploits vulnerabilities on Android operating system in order to gain root privileges on compromised mobile devices.
Hiddad is an Android malware which repackages legitimate apps and then releases them to a third-party store.

"Its main function is displaying ads; however, it is also able to gain access to key security details built into the operating system, allowing an attacker to obtain sensitive user data," Check Point explained.
